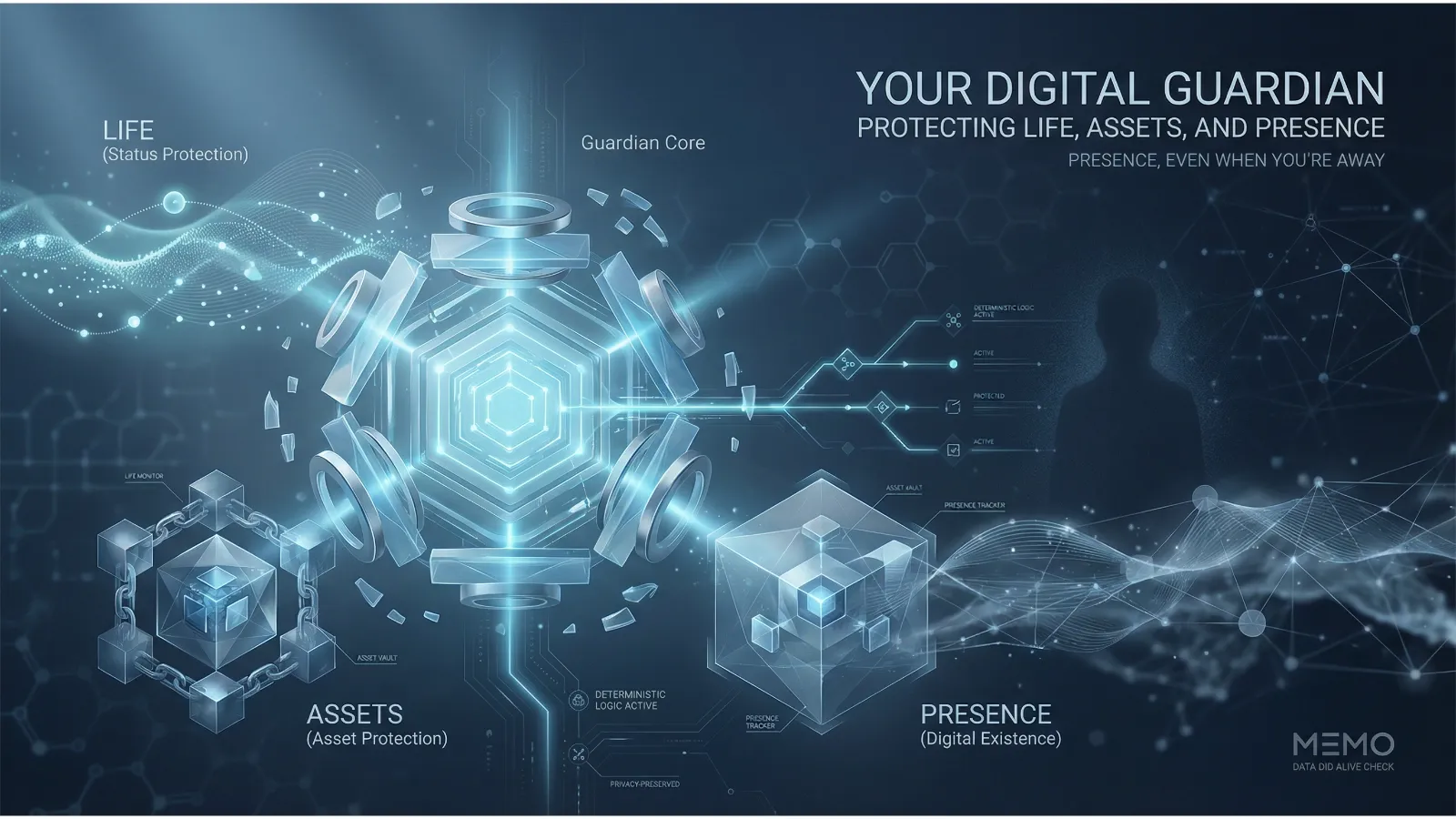
Your Digital Guardian: How MEMO Alive Check Protects Life, Assets, and Presence
1. Rethinking Digital Identity
In today’s hyper-connected world, our digital selves have become as important as our physical presence. Social accounts, cloud files, crypto wallets, and decentralized identities collectively define who we are online. Yet while visibility has increased, the assurance of presence remains fragile.
Traditional digital identity systems are static—they confirm who you are but do not act when you are absent. MEMO’s Data DID challenges this notion by introducing Alive Check, a Web3-native module that transforms digital identity from a passive credential into a living, caring guardian. Alive Check doesn’t just track; it ensures your presence is acknowledged, your assets protected, and your responsibilities fulfilled even when you cannot actively act.
2. The Challenge of Absence
Life is unpredictable. Sudden illness, accidents, or unforeseen events can render a user unreachable. In traditional systems, absence often translates to locked accounts, inaccessible assets, or lost data, creating permanent digital limbo.
Alive Check addresses this head-on. Unlike simple “Are you alive?” apps, it operates entirely on-chain, recording all actions immutably. It integrates real-world contingencies with deterministic digital protocols, ensuring that absence is not a point of failure but a managed event.
3. Core Mechanisms: From Status Sync to Deterministic Delivery
Safety Report: Minimalist Daily Check-In
Users submit a daily Safety Report through the Data DID dashboard. This simple check-in confirms well-being and updates the system about the user’s status. The minimalist approach avoids intrusion while forming the backbone of automated protection.
Tiered Alert System: Gentle to Deterministic
Alive Check features a multi-layered alert logic:
- Day 1: No check-in triggers a gentle reminder.
- Day 2 (48 hours): Absence triggers pre-set instructions. Trusted contacts receive encrypted alerts with actionable information.
Deterministic Asset and Data Management
When the user is determined to be unreachable, the system executes predefined protocols:
- Asset transfer or retrieval instructions are sent to designated contacts.
- Sensitive data can be selectively destroyed or securely redirected.
- Chain-based recording guarantees transparency, immutability, and trustless operation.
This ensures that digital assets and personal responsibilities are handled predictably and securely, mitigating risk and uncertainty.
4. Privacy-First Design
Sensitive life-status information requires careful handling. MEMO emphasizes user autonomy and privacy:
- Local encryption: All Safety Reports and authorization data remain encrypted locally; the MEMO network never tracks irrelevant user behavior.
- Customizable control: Users define emergency contacts, message templates, and optional modules such as location sharing.
This approach positions Alive Check not as a surveillance system, but as a respectful guardian, combining protection with discretion.
5. Integrating Tokenized Engagement
Alive Check also introduces points-based subscription activation, a first for MEMO:
- Users can unlock long-term safety services using 1,000 accumulated points, lowering the entry barrier to security.
- Points serve as fuel for running AI Agents and accessing advanced services, embedding the safety mechanism within MEMO’s broader tokenized ecosystem.
This integration transforms digital safety into a dynamic, interactive experience, connecting incentives, functionality, and responsibility.
6. AI Agents: The Second Safety Brain
The true potential of Alive Check unfolds with MEMO’s AI Agent platform:
- AI Agents act as autonomous “second brains,” monitoring both digital and real-world signals.
- Upon detecting prolonged absence, they can automatically handle:
- Chain-based asset liquidation or transfer
- Targeted data destruction or redirection
- Communication with designated contacts in real time
This elevates Data DID from a static identity to a proactive, intelligent guardian, capable of executing complex instructions without user intervention.
7. Beyond Individuals: Community and Ecosystem Impact
Alive Check is not just about personal safety—it reshapes collective digital trust:
- Families, teams, and decentralized communities can rely on automated continuity and oversight.
- Absence becomes a managed event rather than a system vulnerability.
- Digital identities evolve into nodes of care, responsibility, and resilience.
8. The Future of Digital Guardianship
MEMO Alive Check redefines digital identity as more than a proof of existence—it is a living presence that cares. By combining blockchain transparency, privacy-first design, automated delegation, tokenized engagement, and AI-driven monitoring, it creates a comprehensive safety net.
In this vision, absence is no longer synonymous with loss. Digital identities can safeguard lives, preserve assets, and ensure continuity of responsibility. MEMO Data DID and Alive Check do not merely manage digital identity—they extend human care into the digital realm, shaping a future where presence, protection, and trust are inseparable.
Frequently Asked Questions (FAQs)
Q1:What is MEMO?
MEMO is a Web3 data infrastructure platform that combines decentralized storage, decentralized identity, and data-market primitives to enable user-owned data, privacy-preserving services, and AI-native applications—forming the foundation for DePAI systems and autonomous, economically active AI agents.
Q2:What is MEMO DID?
MEMO DID is MEMO’s decentralized identifier system that issues verifiable, portable identities for people, organizations, and AI agents, enabling authorization, recovery, and delegated access.
Q3:What is MEMO Data DID as a product?
MEMO Data DID is a self-sovereign decentralized identity product where users create and own a persistent digital identity that can be used across Web3 applications, data services, and ecosystem events without relying on centralized logins.
Q4: How does Data DID improve security compared to traditional accounts?
Data DID gives users full control over their identity and credentials, reducing reliance on central platforms and minimizing risks of data leakage, account takeovers, and third-party breaches.
Q5: How does Data DID help AI agents interact securely?
AI agents can authenticate using a DID and receive scoped capabilities and access rights, enabling secure automated workflows.
